SearchStax Cloud – Recommended Mitigation for Solr Vulnerability from CVE-2022-39135

December 05, 2022
Dipsy Kapoor
|
SearchStax is proud to announce the winners of the 2022 Partner Excellence Award. The annual Partner Excellence Award showcases innovative digital transformations that SearchStax’s partners achieve for their clients and the overall strategic importance of alliances.
Description of Solr Vulnerability – CVE-2022-39135
Apache Calcite has a vulnerability, CVE-2022-39135, that is exploitable in Apache Solr in SolrCloud mode. If an untrusted user can supply SQL queries to Solr’s “/sql” handler (even indirectly via proxies / other apps), then the user could perform an XML External Entity (XXE) attack.
An XXE attack may lead to the disclosure of confidential data, denial of service, server-side request forgery (SSRF), port scanning from the Solr node, and other system impacts.
Apache Solr versions 6.5 to 8.11.2 are affected by this vulnerability.
Recommended Mitigation for CVE-2022-39135
As recommended by the Apache Solr website, any of the following steps should help prevent this vulnerability from being exploited in your Solr deployment:
- Protect your Solr instance against unauthorized access
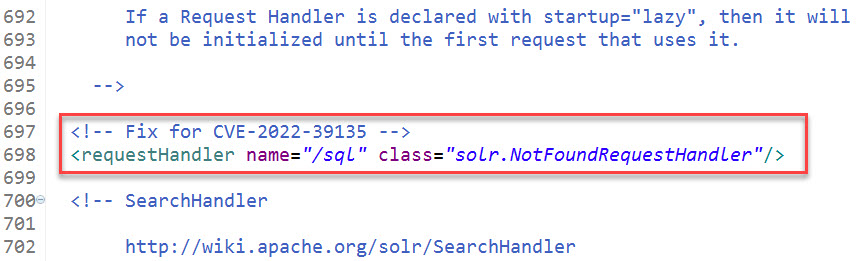
- If you do not use JDBC/the “/sql” handler, it is recommended to disable it by adding the following to your solrconfig.xml:
<requestHandler name="/sql" class="solr.NotFoundRequestHandler"/>
We recommend adding this configuration just before the SearchHandler section around line 697. (Your line numbers may differ.)
What Do I Need to Do to Prevent Vulnerability to CVE-2022-39135?
SearchStax Cloud provides Cloud Private environments, IP Filtering, and Basic Authentication to secure your deployments and recommends using these Security settings whenever possible.
- Review all your Solr deployments – SearchStax customers should review all deployments (production and non-production) and ensure they are protected by IP Filtering and/or Basic Authentication. You can access these settings from SearchStax Dashboard. For more information, refer to SearchStax Cloud documentation for Securing Solr Deployments with SearchStax Cloud.
- Disable /sql Handler – If you do not use the /sql handler, then you should disable it in your solrconfig.xml file. Note that the “/sql” handler is a Solr implicit handler. So, even if you do not have “/sql” handler defined in your configs, it is present and you would need to disable it. Please see the How can I update my Solr Configuration page for instructions on how to update your config files.
- Sitecore Plugin has already disabled “/sql” handler – SearchStax has updated the default configs used by the Sitecore Plugin to disable the “/sql” handler.
If you have any other questions about the Solr Vulnerability, please contact SearchStax Support or submit a support ticket.
By Dipsy Kapoor
VP, Engineering
“…search should not only be for those organizations with massive search budgets...”
Get Our Newsletter
The Stack is delivered bi-monthly with industry trends, insights, products and more