Jan. 30, 2018
admin
|
Does the Meltdown Patch affect Apache Solr performance? OS patches are available which mitigate the possibility of attacks due to Meltdown and Spectre. However, there have been some claims [1, 2], that these fixes can significantly hamper application performance. We wanted to see if there was a performance hit in the case of Solr deployments, and set up experiments to test this.
Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715) are some of the most widespread security issues in modern computing history, affecting almost every computer built in the last 10 years. These vulnerabilities stem from a CPU hardware architecture design flaw that affects billions of devices. Through this flaw, links can be established between user and kernel memory pages, allowing attackers to obtain access to sensitive information.
Experiment Setup
Machine Setup
To test if Meltdown + Spectre patches affect Solr performance, we installed Solr on 2 AWS EC2 instances. The first instance contained a Linux kernel without the patch (4.4.0-97-generic), and the second instance contained kernel with the patch (4.4.0-109-generic). The machines were m4.large class machines running as dedicated hosts, configured with 8G RAM, 2 CPUs , and 8GB of SSD storage. We installed Solr 7.2.1 on each instance, and used SolrMeter as our client for performance tests. The EC2 machines were run in Amazon’s Northern California datacenter, and the test client was executed in Southern California.
Solr Warmth
When executing queries against Solr, it is important to note that one can expect a significant difference in the performance between a “cold” Solr, and a “warm” Solr. A cold Solr is one which has been freshly started. In this case, Solr caches are empty, in an unwarmed state. In contrast, a warm Solr has had it’s caches warmed up. We can expect warm Solrs to perform significantly better than cold Solrs.
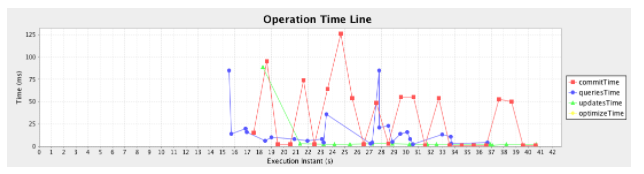
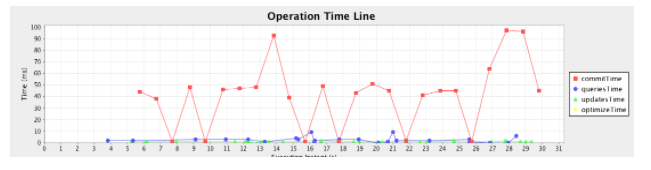
The two graphs below illustrate the difference in performance between warm and cold Solrs. In the cold Solr case, query times vary a lot, and average around 25ms. In the warm Solr case, query times are consistently under 10ms.
Cold Solr
Warm Solr
Trials
We ran 10 trials of 20 seconds each for the following cases:
- Cold Solr, pre-meltdown
- Cold Solr, post-meltdown
- Warm Solr, pre-meltdown
- Warm Solr, post-meltdown
In each trial, we ran queries and updates simultaneously at a rate of 1 QPS.
Experiment Results
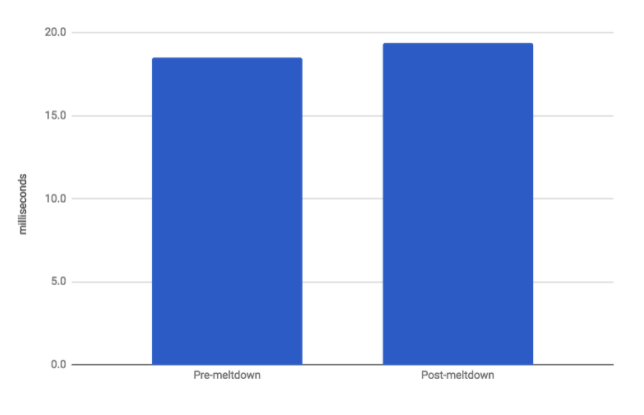
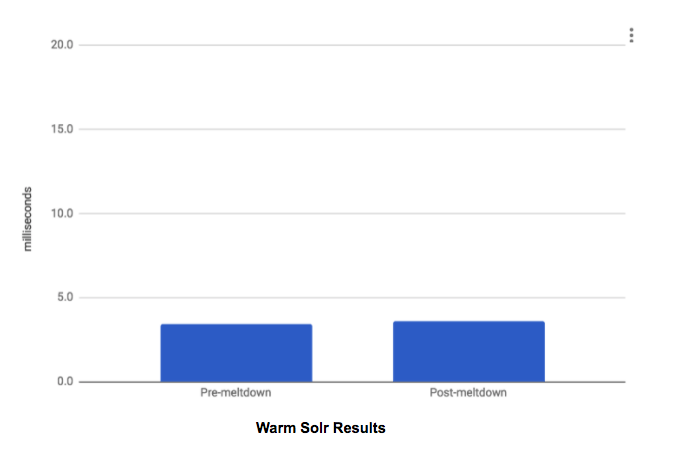
The experimental results are presented in the charts below. In the cold Solr case,
Pre-meltdown average query time was 18.5 ms and post-meltdown time was 19.4 ms. In the warm Solr case, pre-meltdown query time was 3.4 ms and post-meltdown time was 3.6 ms. In both the cold and warm cases, there was not a statistically significant difference between the pre-meltdown and post-meltdown times.
Cold Solr Results
Warm Solr Results
Summary
The Meltdown and Spectre vulnerabilities are a serious security risk that can be solved by OS patching. Several sources have reported that patching the OS can result in a performance hit to applications. In our tests of Solr, we did not find any significant degradation due to the patches. Further testing of various scenarios would be required to determine if there is a performance degradations under certain conditions.